fwsnort: Application Layer IDS/IPS with iptables
fwsnort parses the rules files included in the SNORT ® intrusion detection system and builds an equivalent iptables ruleset for as many rules as possible. fwsnort utilizes the iptables string match module (together with a custom patch that adds a --hex-string option to the iptables user space code which is now integrated with iptables) to detect application level attacks.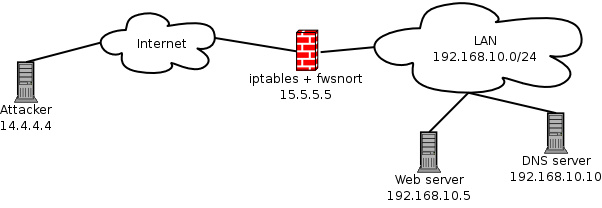
fwsnort was the subject of a featured security article "Basic Intrusion Prevention using Content-based Filtering" on linuxsecurity.com, and has also appeared in SysAdmin Magazine in the article "Content Filtering and Inspection with fwsnort and psad". fwsnort is also featured in the book " Troubleshooting Linux(R) Firewalls" by Michael Shinn and Scott Shinn, and published by Addison Wesley, and a complete treatment of fwsnort can be found in " Linux Firewalls: Attack Detection and Response with iptables, psad, and fwsnort" published by No Starch Press.
Data replacement patches for the iptables string match extension can be found here (2.4 kernels only): libipt_string patch, ipt_string kernel patch. Together these patches emulate the replace keyword in Snort_inline by adding two new iptables command line options, "--replace-string" and "--replace-hex-string". All data replacement is performed within the kernel. See my DEFCON 12 presentation for more information.
Here is an example of a translated Snort ® rule from the /etc/fwsnort/fwsnort.sh script that fwsnort builds. This is a basic Snort ® rule that looks for attempts to execute the gcc compiler via a webserver, and note how fwsnort uses the string match extension as well as the iptables comment match (so that the rule ID is included whenever the iptables policy is listed from the command line):
### alert tcp $EXTERNAL_NET any -> $HTTP_SERVERS $HTTP_PORTS (msg:"WEB-ATTACKS /usr/bin/gcc command attempt"; flow:to_server,established; content:"/usr/bin/gcc"; nocase; classtype:web-application-attack; sid:1341; rev:5;)
$IPTABLES -A FWSNORT_FORWARD_ESTAB -p tcp --dport 80 -m string --string "/usr/bin/gcc" --algo bm -m comment --comment "sid:1341; msg:WEB-ATTACKS /usr/bin/gcc command attempt; classtype:web-application-attack; rev:5; FWS:1.0.2;" -j LOG --log-ip-options --log-tcp-options --log-prefix "[5] SID1341 ESTAB "
$IPTABLES -A FWSNORT_INPUT_ESTAB -p tcp --dport 80 -m string --string "/usr/bin/gcc" --algo bm -m comment --comment "sid:1341; msg:WEB-ATTACKS /usr/bin/gcc command attempt; classtype:web-application-attack; rev:5; FWS:1.0.2;" -j LOG --log-ip-options --log-tcp-options --log-prefix "[5] SID1341 ESTAB "
Snort is a registered trademark of Sourcefire, Inc.




